The Basics of Cyber Security Penetration Testing: Part 1
In this article I will explore some of the most common cyber-attack types and discuss strategies on how to stop them. Please be aware that the attack methods demonstrated here should not be used unless you have explicit written permission from the targeted company.
1. Scanning systems for vulnerabilities.
Before any attack, there is a passive and active reconnaissance phase to discover more information about the company and the devices you are planning to attack. The best approach is to find a known vulnerability and target it!
The Passive phase is usually undetectable by any security system as it involves researching the company using Google or other search engines. For instance, like Shodan might reveal a web camera accessible via the internet with default credentials or outdated software laden with vulnerabilities ripe for exploitation. Additionally, examining the company website using browser developer tools can yield valuable insights. Tools such as NsLookup or Dig, along with WhoIs databases, are instrumental in researching company DNS records and IP addresses. There are also tools like CeWL that crawl a website and generate lists that can be used for brute-force attacks. However, I consider this tool part of the active reconnaissance as it can be detected as a web scraping attack.
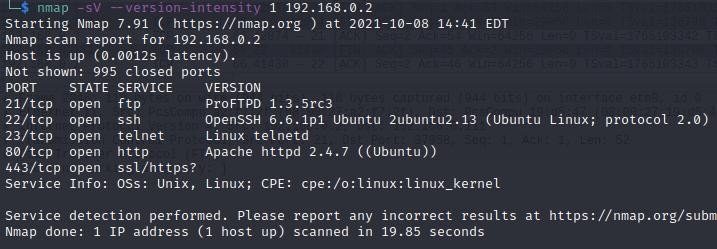
In the Active phase, the focus shifts to identifying vulnerabilities on the desktops, servers, or websites. This phase requires caution, as if we are not careful, we can be detected. A popular scanning tool is Nmap, which can discover hosts, their opened ports, and even specific details like the operating system versions or services running (e.g., Apache, SSH, FTP, SMB, etc). Using options like ‘-A’ allows for simultaneous service and OS scans – most options can be found here: Options Summary | Nmap Network Scanning. Nmap also has scripts with the Nmap Scripting Engine (NSE) that can be used to exploit vulnerabilities, and the default scripts can be triggered with the ‘-sC’ option. There is an ‘-sS’ option for silent scans, where Nmap will send RST instead of ACK at the end of the TCP handshake.
There is a GUI version on Nmap called Zenmap that can be installed on Windows.
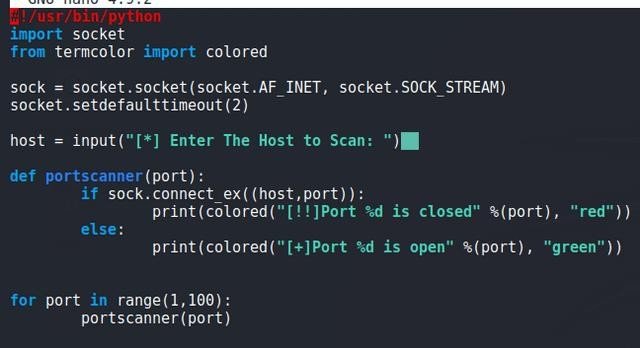
Custom Python scripts are a versatile tool for port scanning, with many examples available on the internet. These scripts often utilize the sockets library, which allows for the construction of IP packets with fewer limitations compared to other Python libraries. For more complex needs, Scapy is an excellent tool that can craft various types of IP packets. Scapy is available as a Python library if needed when the functionality of sockets alone are not enough. There are lots of Python port scanner scripts on the internet and articles available, such as: How to write a port scanner in Python in 5 minutes: Example and walkthrough | Infosec (infosecinstitute.com)
Scanners like OpenVAS or Nessus are powerful tools for conducting automated scans across various vulnerabilities and protocols, including HTTP web vulnerabilities. There are several informative YouTube tutorials that demonstrate how to effectively use these scanners. Large companies often deploy agents such as Qualys in their environments to conduct periodic scans. However, caution is advised when using auto-scanning tools; they generate a high volume of requests, which can trigger not only detection for port sweeps but also DOS alarms. It’s important to ensure these scans do not inadvertently activate DOS defenses.
After this we can use a database such as SearchSploit in Kali, or the online databases like exploit-db and MITRE ATT&CK, to identify vulnerabilities and test them against the web server, shifting from active to passive reconnaissance until the server is successfully exploited.
For those interested in learning more about pentesting, TryHackMe offers training materials: TryHackMe | CompTIA Pentest+ Training
How do we stop such attacks? The most popular methods are:
As I previously mentioned, it is challenging to protect against passive reconnaissance. However, it is crucial to ensure that your web pages do not contain sensitive information in files, hidden comments, or parameters visible with developer tools; hence, maintaining clean code is key. Additionally, using a reverse web proxy like F5 AWAF/ASM with DLP functions can help scrub sensitive content, such as credit card numbers inadvertently exposed on web pages.
For active reconnaissance, attackers typically begin with tools such as Nmap or a Python script to scan for open ports. These port scans can be detected by systems like IPS, NDR, NGFWs such as Palo Alto, or ADCs like F5 BIG-IP AFM. Older security systems could be fooled by randomizing port scans in Nmap or Python scripts. However, more advanced network security systems are designed to recognize and respond to the unusual volume of port requests from a single IP address within a specific timeframe.
2. Vulnerability attacks and infected file downloads or uploads
A popular tool used by attackers is the Metasploit framework which can exploit many vulnerabilities on the target devices and then create different attack payloads for Linux, Windows or mobile platforms. These payloads can be used for tasks such as data exfiltration or uploading a shell to gain full control of the target system. There are other exploitation frameworks like Empire or even Nmap, but Metasploit remains very popular.
Infected files can contain viruses, trojans or worms. A virus is a type of software or computer program that attaches itself to another software or computer program to harm the computer system, and this is called a shell. There are two popular types of shells: bind and reverse. The bind shell opens up a new service on the target machine and requires the attacker to connect to it to get a session. On the other hand, a reverse shell, also known as a connect-back, operates by having the attacker set up a listener on their own system first. The target machine then acts as a client that connects to this listener, allowing the attacker to gain control. Reverse shells are particularly dangerous as they can often bypass older security systems. This is especially true in networks where the Zero Trust model is not fully implemented, allowing outbound traffic from the infected device to any destination on the internet, which then poses a significant threat.
Additionally, Msfvenom can be used independently of the Metasploit framework to create malicious payloads. These payloads can then be compiled into C programs using tools like GCC, making them harder to detect and more dangerous.
There is a free course for the Metasploit framework that anyone can check out here Metasploit Unleashed | Metasploit Unleashed - Free Online Ethical Hacking Course | OffSec, from this you can learn how to migrate the meterpreter shell to a process with more permissions for privilege escalation and persistence, export windows reg keys, trigger keyboard logger and even deleting the logs on a computer, so after you exit the device there will be no trace of your actions.
How do we stop such attacks? The most effective methods include:
Inline Blocking of Vulnerabilities: Systems like F5 AFM, Palo Alto NGFW, and for web vulnerabilities, F5 AWAF/F5 XC WAAP, are employed to block vulnerabilities directly. The bad payloads are blocked with antivirus and sandboxing emulations on the NGFW devices like Palo Alto and their Wildfire cloud sandboxing or integrations with such systems through the ICAP protocol from SWG or ADC like F5 BIG-IP. Nowadays, with SaaS cloud cyber security platforms like F5 XC Distributed Cloud, you can install a container of your choice like ClamAV or, even better, OPSWAT MetaDefender Core Container in Kubernetes environment, and this is how the web file uploads and downloads will be scanned after HTTPS decryption.
Endpoint Protection: Antivirus software or, more effectively, an EDR (Endpoint Detection and Response) agent on your computer handles security breaches that bypass perimeter defences, such as those from a USB flash drive or cases where SSL decryption is not performed on ADCs or NGFWs. Secure Customer Edge Cloud services like Palo Alto Prisma Access SASE are also utilized.
Interrupting Command and Control (C&C) Channels: In some cases, even if malicious files are installed, it's not necessarily a complete breach. NGFW systems can disrupt the C&C channels. For example, in the Metasploit framework, the most popular shell is called Meterpreter and it uses SSL/TLS encryption. By enabling outbound SSL decryption on your NGFW or SWG, you can allow for the decryption of outbound traffic and the activation of vulnerability signatures in systems like Palo Alto NGFW. This action blocks the shell from reaching the attacker's server, effectively breaking the attack.
Author: Nikolay Dimitrov